A few of these checks are applied from the Predator installation server, and a few are implemented by code that Predator operates about the user’s device.
For the reason that spy ware is often priced on the for every-infection foundation, it is usually undesirable for operators to hazard installation on unintended targets by submitting an infection inbound links publicly. Using such replies possible factors to an absence of professionalism or of problem for the possibilities of receiving caught.
The scientists mention that Predator is distributed by means of cropped hyperlinks connected to phishing e-mail. In the event the concentrate on person clicks on these back links, They're redirected to the destructive area where the Alien malware is delivered, dropping the Predator payload.
If you need to be absent from the Personal computer, you get rid of the USB generate which will disable the keyboard, mouse and darken the monitor. Upon returning all of that you'll want to do is insert the flash generate and every thing is restored.
Engage in all sides off against each other inside a series of exceptional three-way on the internet modes and go tooth-to-claw-to-pulse rifle while in the reinvention of one of multiplayer gaming's defining moments.
bundled Cytrox Predator infection back links in replies to numerous U.S. and Worldwide officers and others.
We've these types of sizzling gay intercourse we go all night time alongside jerking our dicks to banning those who disagree with us contact us out or simply just simply wanna troll and have fun.
Hotkey Integration: Customize hotkeys for speedy usage of important characteristics, allowing you for ssz predator making adjustments without the need of interrupting your gameplay.
The technical storage or accessibility that is employed exclusively for statistical purposes. The specialized storage or entry that is certainly used exclusively for nameless statistical purposes.
The videos under showcases the smoothness of the goal lock and its adjustable fashion engineered to assist for aiming in any kind of activity.
The corporate, which Boston-centered non-public equity business Bain Funds acquired for $5.6 billion in October, has confronted a barrage of lawsuits because it acknowledged the attack in January. The most recent escalation could open it to better authorized exposure.
When your buy position altered to "Paid out" you may then you can locate your keys at "Shop-Deal with Buys" over the navigation bar. FAQ : Why is my payment pending for evaluation and using so prolonged?
! I had to get a waffle cone dipped in chocolate and coated in sprinkles naturally had to celebrate passing my NASM examination , sprinkles many of the way!!!
If a consumer clicked on one of many hyperlinks, in addition to a validation method (see: Section 2) was satisfied, the consumer’s device might have been contaminated with Cytrox’s Predator spyware, possible using a chain of zero-working day exploits. Cytrox is actually a subsidiary of surveillance conglomerate Intellexa.
 Taran Noah Smith Then & Now!
Taran Noah Smith Then & Now! Ariana Richards Then & Now!
Ariana Richards Then & Now!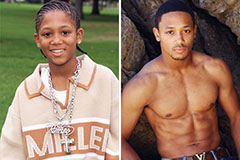 Romeo Miller Then & Now!
Romeo Miller Then & Now! Julia Stiles Then & Now!
Julia Stiles Then & Now! Lynda Carter Then & Now!
Lynda Carter Then & Now!